tcpdump用于捕獲和分析網(wǎng)絡(luò)流量。系統(tǒng)管理員可以使用它來查看實時流量或?qū)⑤敵霰4娴轿募胁⒃谝院筮M行分析。下面列出6個常用選項。
-D 選項
tcpdump的
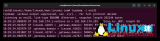
-D獲取接口設(shè)備列表。看到此列表后,可以決定要在哪個接口上捕獲流量。它還告訴你接口是否已啟動、正在運行,以及它是否是環(huán)回接口,如下所示:
[root@localhost~]#tcpdump-D
1.ens160[Up,Running]
2.lo[Up,Running,Loopback]
3.any(Pseudo-devicethatcapturesonallinterfaces)[Up,Running]
4.bluetooth-monitor(BluetoothLinuxMonitor)[none]
5.nflog(Linuxnetfilterlog(NFLOG)interface)[none]
6.nfqueue(Linuxnetfilterqueue(NFQUEUE)interface)[none]
7.usbmon0(AllUSBbuses)[none]
8.usbmon1(USBbusnumber1)
9.usbmon2(USBbusnumber2)
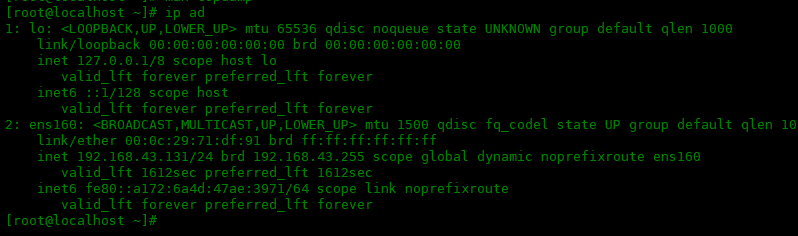
-c [數(shù)字]選項
-c選項捕獲X個數(shù)據(jù)包,然后停止。否則,tcpdump 將無限地繼續(xù)運行。因此,當(dāng)只想捕獲一小部分數(shù)據(jù)包樣本時,可以使用此選項。但是如果接口上沒有數(shù)據(jù)流量,tcpdump 會一直等待。
[root@localhost~]#tcpdump-c5-iany
droppedprivstotcpdump
tcpdump:verboseoutputsuppressed,use-vor-vvforfullprotocoldecode
listeningonany,link-typeLINUX_SLL(Linuxcooked),capturesize262144bytes
1747.713379IPlocalhost.localdomain.ssh>192.168.43.1.39970:Flags[P.],seq714380127:714380371,ack1854022435,win388,length244
1747.713785IPlocalhost.localdomain.36821>_gateway.domain:36365+PTR?1.43.168.192.in-addr.arpa.(43)
1747.713939IP192.168.43.1.39970>localhost.localdomain.ssh:Flags[.],ack244,win4104,length0
1747.716053IP_gateway.domain>localhost.localdomain.36821:36365NXDomain0/1/0(78)
1747.716543IPlocalhost.localdomain.57441>_gateway.domain:61445+PTR?131.43.168.192.in-addr.arpa.(45)
5packetscaptured
9packetsreceivedbyfilter
0packetsdroppedbykernel
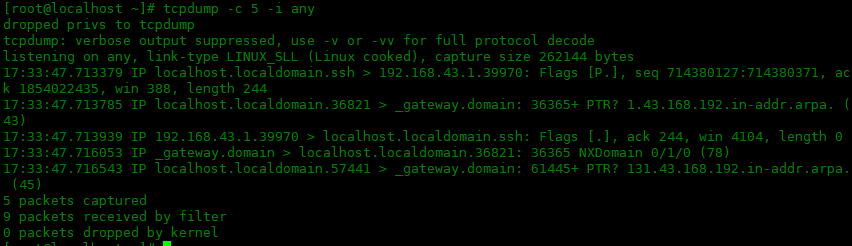
-n 選項
-n選項不將IP地址解析為域名,直接以IP地址顯示:
[root@localhost~]#tcpdump-c5-iany-n
droppedprivstotcpdump
tcpdump:verboseoutputsuppressed,use-vor-vvforfullprotocoldecode
listeningonany,link-typeLINUX_SLL(Linuxcooked),capturesize262144bytes
1738.980756IP192.168.43.131.ssh>192.168.43.1.39970:Flags[P.],seq714383039:714383283,ack1854024303,win388,length244
1738.981032IP192.168.43.131.ssh>192.168.43.1.39970:Flags[P.],seq244:440,ack1,win388,length196
1738.981096IP192.168.43.131.ssh>192.168.43.1.39970:Flags[P.],seq440:604,ack1,win388,length164
1738.981153IP192.168.43.131.ssh>192.168.43.1.39970:Flags[P.],seq604:768,ack1,win388,length164
1738.981208IP192.168.43.131.ssh>192.168.43.1.39970:Flags[P.],seq768:932,ack1,win388,length164
5packetscaptured
5packetsreceivedbyfilter
0packetsdroppedbykernel
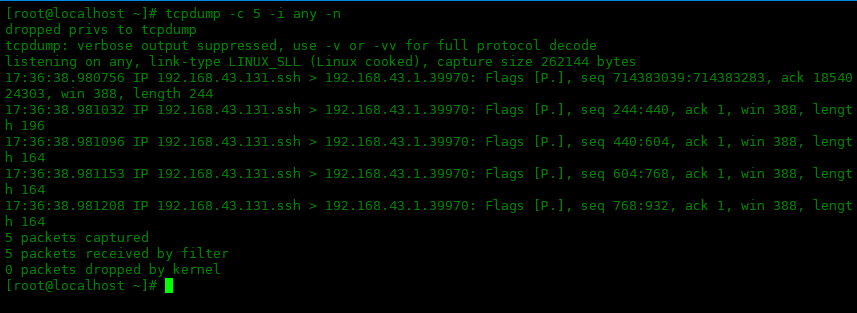
-s 選項
帶有
-sXXX的 tcpdump 可幫助你控制捕獲數(shù)據(jù)包的大小。在上一個輸出的第三行中,可以看到它表示捕獲大小 262144 字節(jié)。可以使用-s選項更改捕獲數(shù)據(jù)大小。如果你只想檢查數(shù)據(jù)包標(biāo)頭,則可以使用較小的大小進行捕獲:
[root@localhost~]#tcpdump-c5-iany-n-s64
droppedprivstotcpdump
tcpdump:verboseoutputsuppressed,use-vor-vvforfullprotocoldecode
listeningonany,link-typeLINUX_SLL(Linuxcooked),capturesize64bytes
1744.437891IP192.168.43.131.ssh>192.168.43.1.39970:Flags[P.],seq714405271:714405515,ack1854033767,win388,length244
1744.438153IP192.168.43.131.ssh>192.168.43.1.39970:Flags[P.],seq244:440,ack1,win388,length196
1744.438220IP192.168.43.131.ssh>192.168.43.1.39970:Flags[P.],seq440:604,ack1,win388,length164
1744.438301IP192.168.43.131.ssh>192.168.43.1.39970:Flags[P.],seq604:768,ack1,win388,length164
1744.438361IP192.168.43.131.ssh>192.168.43.1.39970:Flags[P.],seq768:932,ack1,win388,length164
5packetscaptured
5packetsreceivedbyfilter
0packetsdroppedbykernel
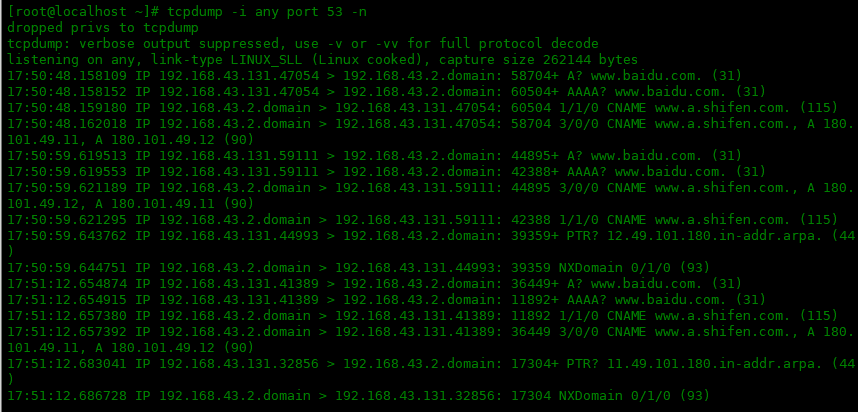
端口捕獲
port選項前加上 src/dst。如src port 53或dst port 53并進一步過濾它。
[root@localhost~]#tcpdump-ianyport53-n
droppedprivstotcpdump
tcpdump:verboseoutputsuppressed,use-vor-vvforfullprotocoldecode
listeningonany,link-typeLINUX_SLL(Linuxcooked),capturesize262144bytes
1748.158109IP192.168.43.131.47054>192.168.43.2.domain:58704+A?www.baidu.com.(31)
1748.158152IP192.168.43.131.47054>192.168.43.2.domain:60504+AAAA?www.baidu.com.(31)
1748.159180IP192.168.43.2.domain>192.168.43.131.47054:605041/1/0CNAMEwww.a.shifen.com.(115)
1748.162018IP192.168.43.2.domain>192.168.43.131.47054:587043/0/0CNAMEwww.a.shifen.com.,A180.101.49.11,A180.101.49.12(90)
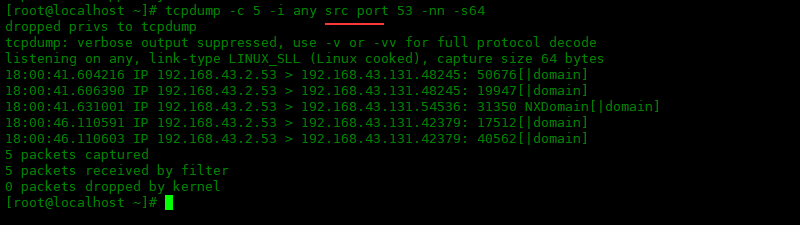
-nn選項表示不解析IP地址和端口:
[root@localhost~]#tcpdump-c5-ianysrcport53-nn-s64
droppedprivstotcpdump
tcpdump:verboseoutputsuppressed,use-vor-vvforfullprotocoldecode
listeningonany,link-typeLINUX_SLL(Linuxcooked),capturesize64bytes
1841.604216IP192.168.43.2.53>192.168.43.131.48245:50676[|domain]
1841.606390IP192.168.43.2.53>192.168.43.131.48245:19947[|domain]
1841.631001IP192.168.43.2.53>192.168.43.131.54536:31350NXDomain[|domain]
1846.110591IP192.168.43.2.53>192.168.43.131.42379:17512[|domain]
1846.110603IP192.168.43.2.53>192.168.43.131.42379:40562[|domain]
5packetscaptured
5packetsreceivedbyfilter
0packetsdroppedbykernel
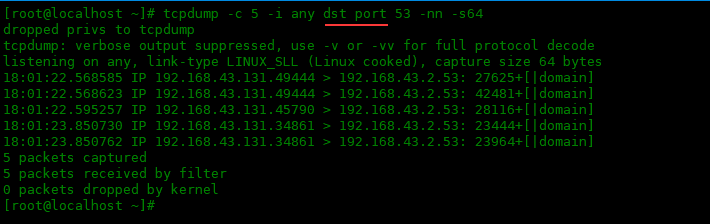
下面只獲取目的端口為53的數(shù)據(jù)包:
[root@localhost~]#tcpdump-c5-ianydstport53-nn-s64
droppedprivstotcpdump
tcpdump:verboseoutputsuppressed,use-vor-vvforfullprotocoldecode
listeningonany,link-typeLINUX_SLL(Linuxcooked),capturesize64bytes
1822.568585IP192.168.43.131.49444>192.168.43.2.53:27625+[|domain]
1822.568623IP192.168.43.131.49444>192.168.43.2.53:42481+[|domain]
1822.595257IP192.168.43.131.45790>192.168.43.2.53:28116+[|domain]
1823.850730IP192.168.43.131.34861>192.168.43.2.53:23444+[|domain]
1823.850762IP192.168.43.131.34861>192.168.43.2.53:23964+[|domain]
5packetscaptured
5packetsreceivedbyfilter
0packetsdroppedbykernel
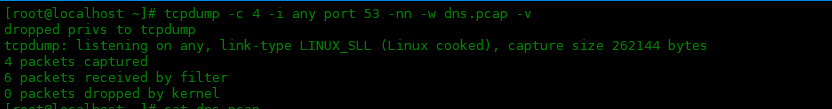
-w 選項
如果要將 tcpdump 的輸出寫入文件,請使用選項
-w選項寫入文件。如果想查看寫了多少數(shù)據(jù)包,可以加-v選項。
[root@localhost~]#tcpdump-c4-ianyport53-nn-wdns.pcap-v
droppedprivstotcpdump
tcpdump:listeningonany,link-typeLINUX_SLL(Linuxcooked),capturesize262144bytes
4packetscaptured
6packetsreceivedbyfilter
0packetsdroppedbykernel
總結(jié)
tcpdump 用于收集有關(guān)網(wǎng)絡(luò)流量數(shù)據(jù)的出色工具。數(shù)據(jù)包捕獲為故障排除和安全分析提供了有用的信息。
原文標(biāo)題:tcpdump 命令的常用選項
文章出處:【微信公眾號:Linux愛好者】歡迎添加關(guān)注!文章轉(zhuǎn)載請注明出處。
審核編輯:湯梓紅
-
接口
+關(guān)注
關(guān)注
33文章
8645瀏覽量
151393 -
網(wǎng)絡(luò)
+關(guān)注
關(guān)注
14文章
7580瀏覽量
88940 -
設(shè)備
+關(guān)注
關(guān)注
2文章
4525瀏覽量
70725
原文標(biāo)題:tcpdump 命令的常用選項
文章出處:【微信號:LinuxHub,微信公眾號:Linux愛好者】歡迎添加關(guān)注!文章轉(zhuǎn)載請注明出處。
發(fā)布評論請先 登錄
相關(guān)推薦
Linux tcpdump命令示例 如何在Linux中安裝tcpdump
tcpdump命令介紹
sd可以實現(xiàn)六個面對應(yīng)六個不同文件夾sd音樂嗎?
六個有關(guān)RoHS的檢測方法標(biāo)準(zhǔn)
linux常用命令實例詳解
tcpdump的安裝以及通過實例來演示如何使用 tcpdump 命令





 詳解tcpdump命令的六個常用選項
詳解tcpdump命令的六個常用選項










評論